QueryPie
Integrated Access Control
Integrated Access Control
Our advanced security solutions deliver the ultimate layer of defense, safeguarding your company’s most critical assets from threats.
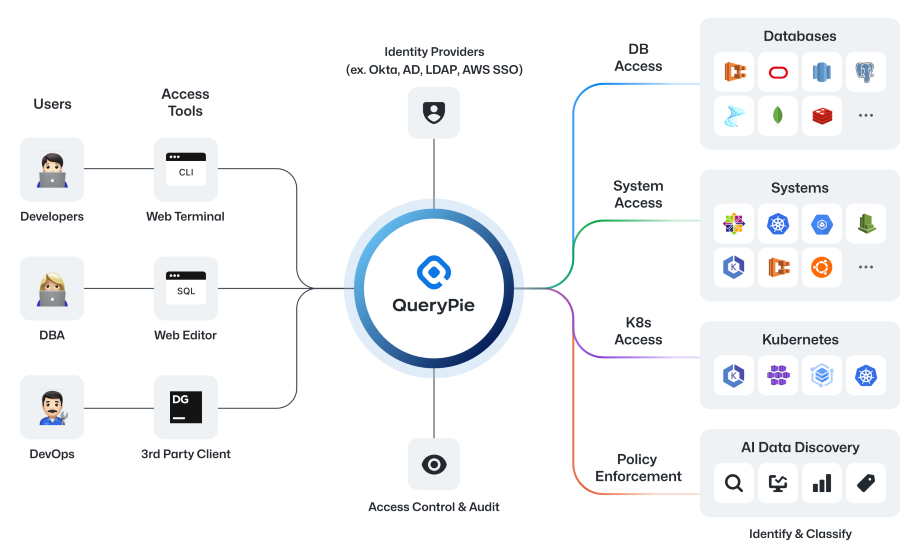
With integrated access control across databases, systems, Kubernetes,
and web applications—all within a unified Zero Trust framework—you gain a comprehensive, all-in-one approach to protection you can trust.
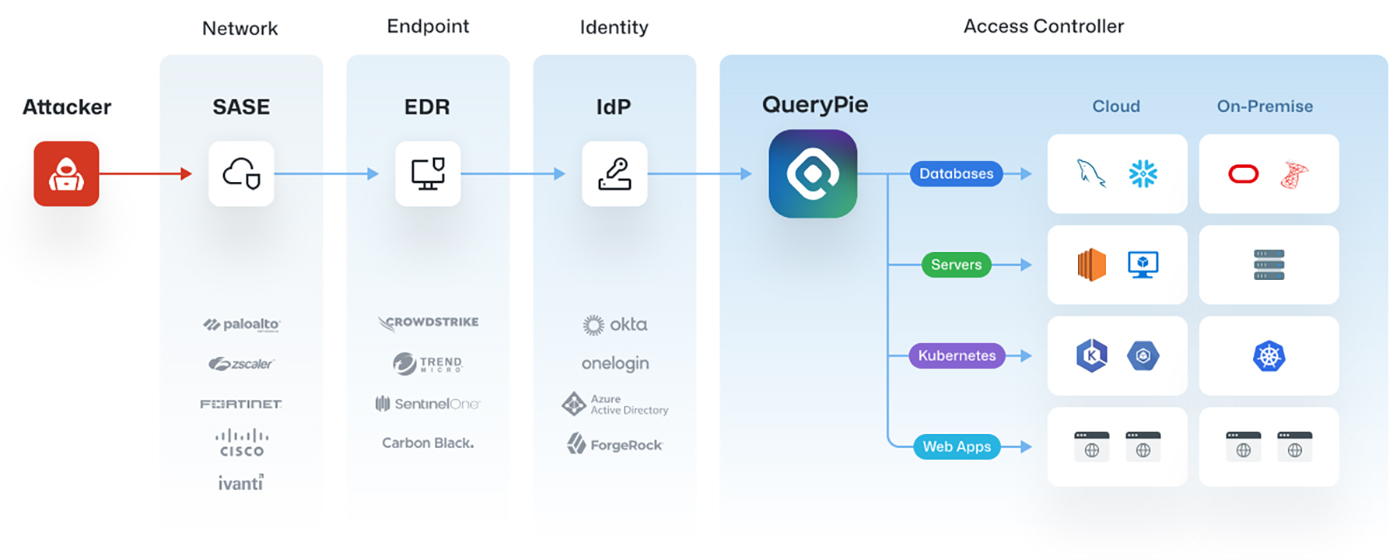
Gain complete visibility and control over your entire infrastructure by casting QueryPie to centralize access control and auditing.
With seamless integration across platforms, manage user access as effortlessly as casting a simple spell!
Enforce your security policies like a pro and keep your important assets secure—whether in the cloud or on-premises!
Managing data access is no walk in the park.
As data governance zooms in from whole warehouses down to individual cells and columns,
figuring out who should see what data gets a whole lot trickier. And when massive data transfers come into play,
making sure each user has just the right access isn’t just essential—it’s a serious juggling act.
Access permissions are in a constant state of shuffle.
With people coming and going, clients switching things up, and org structures always in motion, those access controls need constant updates—a job that’s no small feat. Most organizations still rely on roles or job titles for permissions, but this often means too many privileges and too many risks. Without strict oversight, these extra permissions could leave the door wide open to threats.
Companies are shifting away from a mishmash of security tools and leaning into streamlined, all-in-one platforms from fewer vendors.
QueryPie is on board with this shift, bringing together access control in one cohesive solution. This not only cuts down the hassle of managing different tools but also boosts overall security and operational flow.
Easily manage permissions with our simplified access control, ensuring the right people access the right information to keep your data safe.
Automated auditing and reporting keep your data secure and compliant. Spot issues early with real-time insights and maintain control.
Our solutions enhance engineering processes and streamline productivity, empowering your team to operate at peak performance.
Our solutions simplify compliance, eliminating stress and uncertainty while ensuring your data security standards are met.
Our optimized integration unifies your systems for seamless data access, enhancing efficiency and enabling smarter, faster work.
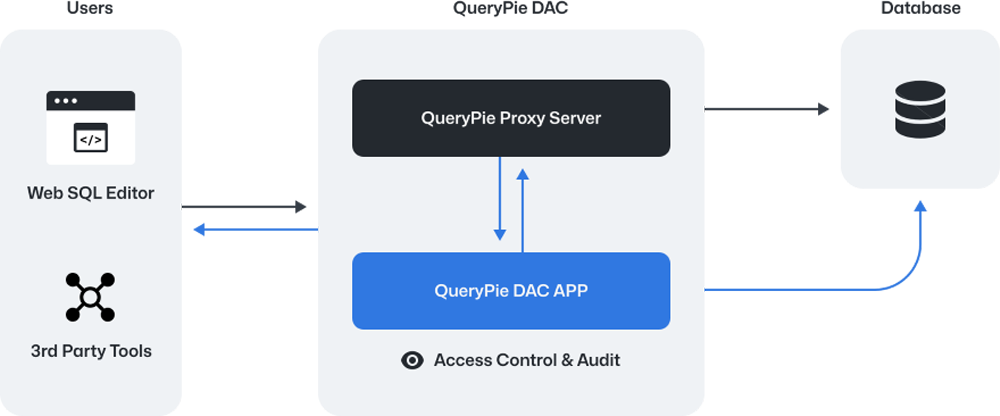
QueryPie DAC is crafted for data protection in the cloud era, seamlessly connecting various cloud ecosystems. It automatically identifies sensitive data and personal information, ensuring robust security for your assets.
Manage access effortlessly with controls based on user roles and attributes like time, day, IP address, SQL type, and more.
Enjoy a web SQL editor that connects you to databases, allowing you to run queries and import/export data directly from your browser—no separate client needed.
Stay informed by tracking user activities, including logins, database access, privilege changes, SQL commands, and query results to catch any unusual behavior.
Protect sensitive information by applying data masking policies and set access limits on important tables and columns with specific query rules.
Request access when you need it, and let admins approve and grant permissions on the spot, with seamless integrations like Slack.
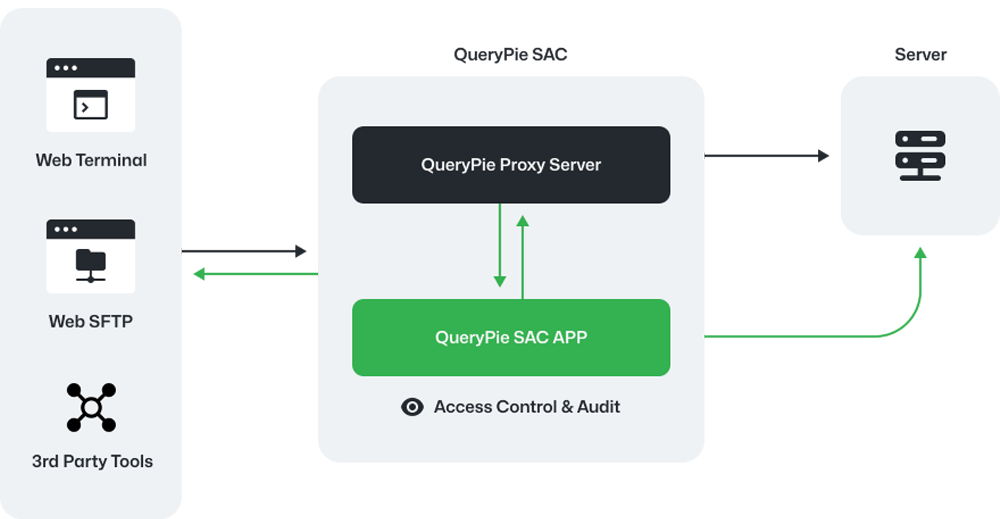
QueryPie SAC is designed for cloud instance protection on AWS, GCP, and Azure, while also supporting on-premises environments. It enables administrators to monitor user commands and replay sessions, enhancing security and oversight across all platforms.
Efficiently manage servers with server group functionality and tag filtering to centrally operate permissions and policies.
Access a web terminal and FTP client for server connections and task execution within web browsers, ensuring consistent access and permission control.
Grant permissions and manage policies across server groups, inheriting settings like access times while enabling flexible management at both server and user levels.
QueryPie provides a desktop agent that allows users to connect to various systems and server equipment through existing access programs.
Manage permissions centrally for all resources, including systems and servers across cloud and on-premises environments, accessible via SSH.
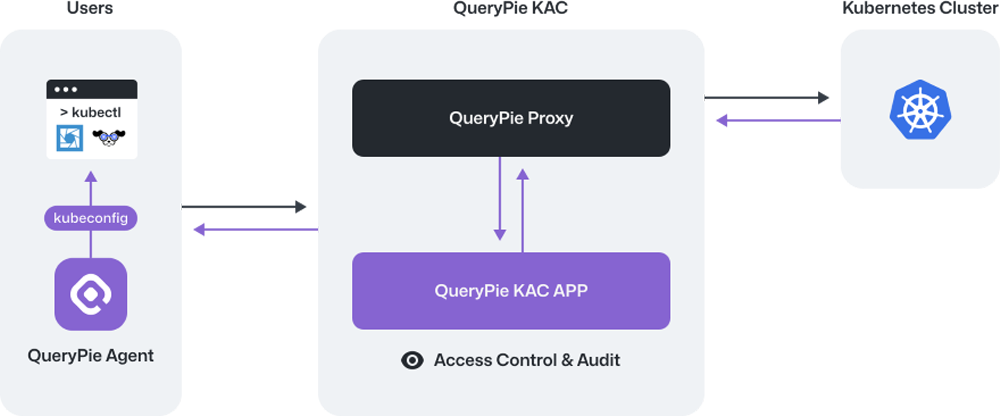
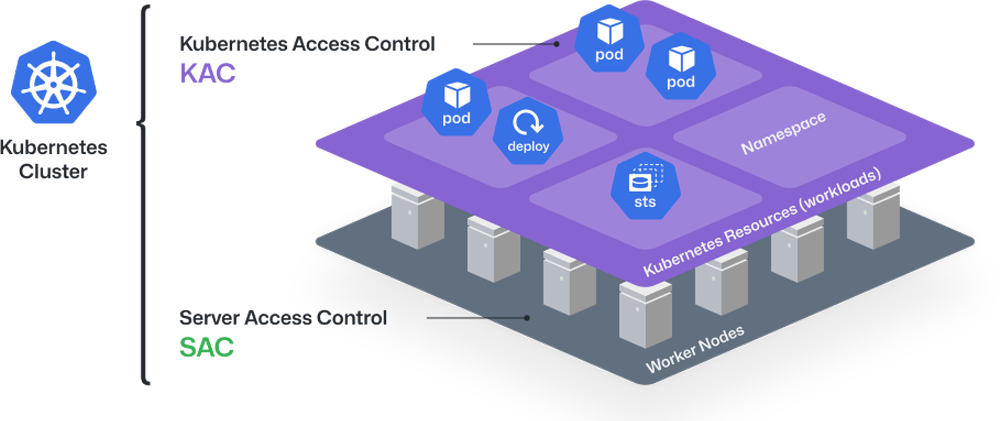
QueryPie KAC is a solution for Kubernetes API protection, enabling centralized management of cloud infrastructures like AWS EKS and on-premises clusters. Administrators can manage access, monitor API requests, and replay container command executions.
Implement role-based (RBAC) access for Kubernetes clusters, managing API access with tailored policies. Use attribute-based (ABAC) conditions to ensure permissions align with specific user attributes.
Automatically register admin access permissions for cloud-based Kubernetes clusters like AWS EKS by simply assigning IAM permissions.
Gain visibility into user actions across multiple clusters in near real-time through audit logs and pod session recordings.
Automatically record sessions when users connect to containers, monitoring their actions. Apply access control rules based on K8S resource names (RegEx) not supported in standard K8S RBAC.
Optimize cloud environments by synchronizing distributed resources and managing multiple Kubernetes integrations. Automate resource synchronization and track change history with scheduling functions.
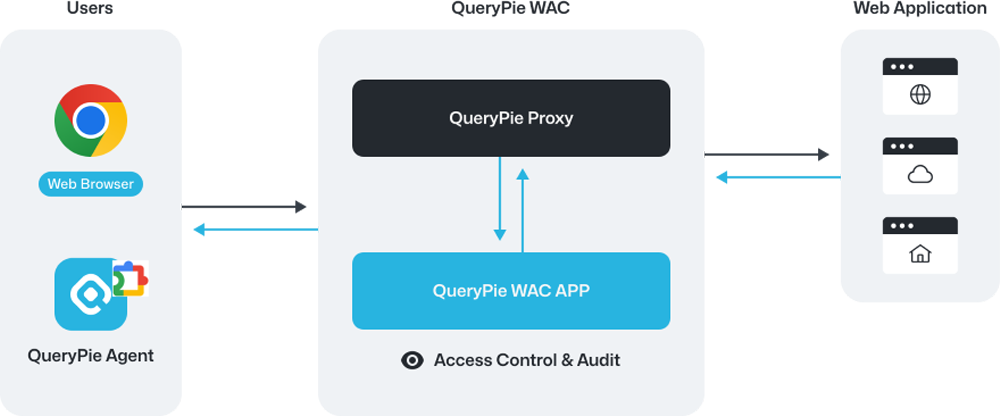
QueryPie WAC secures access and logs activities for web applications, including admin portals and SaaS platforms.
It grants access to authorized users, captures logs and screenshots, masks sensitive data, and controls actions like file transfers.
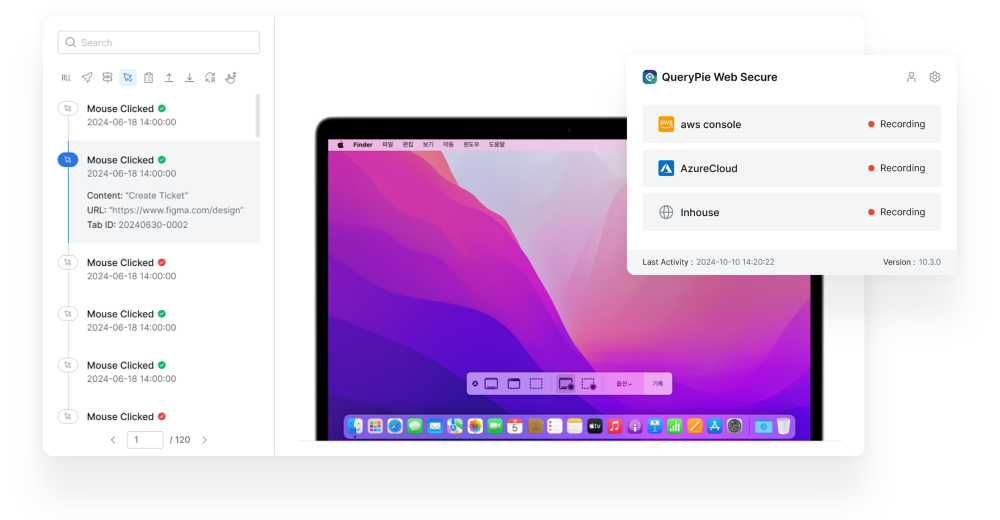
Unite all your web apps, from homegrown solutions to SaaS, to enable RBAC and permission management that fills security gaps.
Record user actions like navigating URLs, clicking links, and copying to the clipboard with screenshots, while analyzing HTTP requests for a clear view of events.
Keep track of user activities, including clicks, typing, clipboard use, and file transfers. Log details like button clicks along with screenshots for easy reviewing.
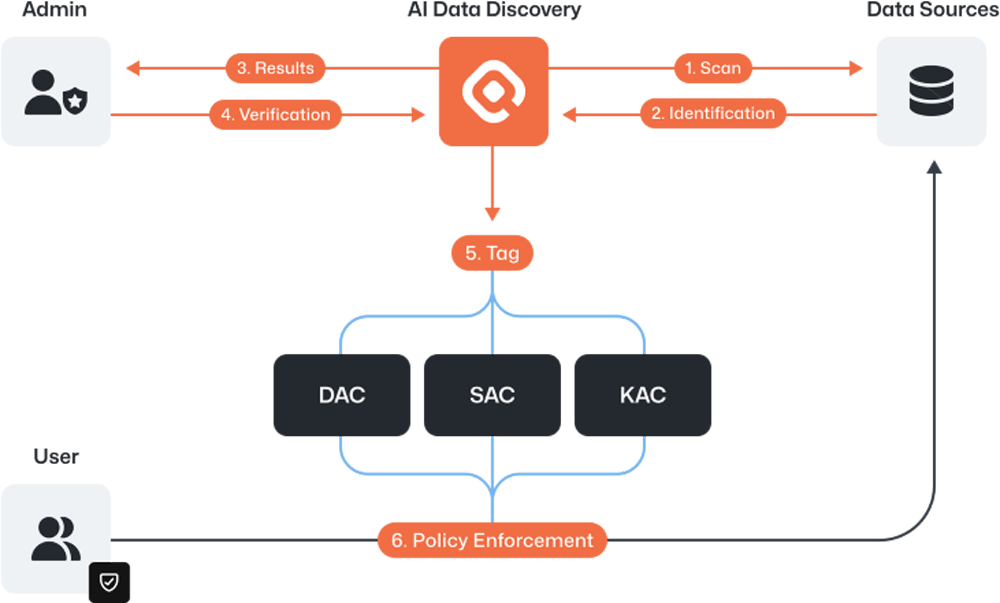
AI-based Data Discovery automatically identifies and
classifies sensitive information, generating tags for access control.
It offers convenient visibility through a dashboard and inventory.
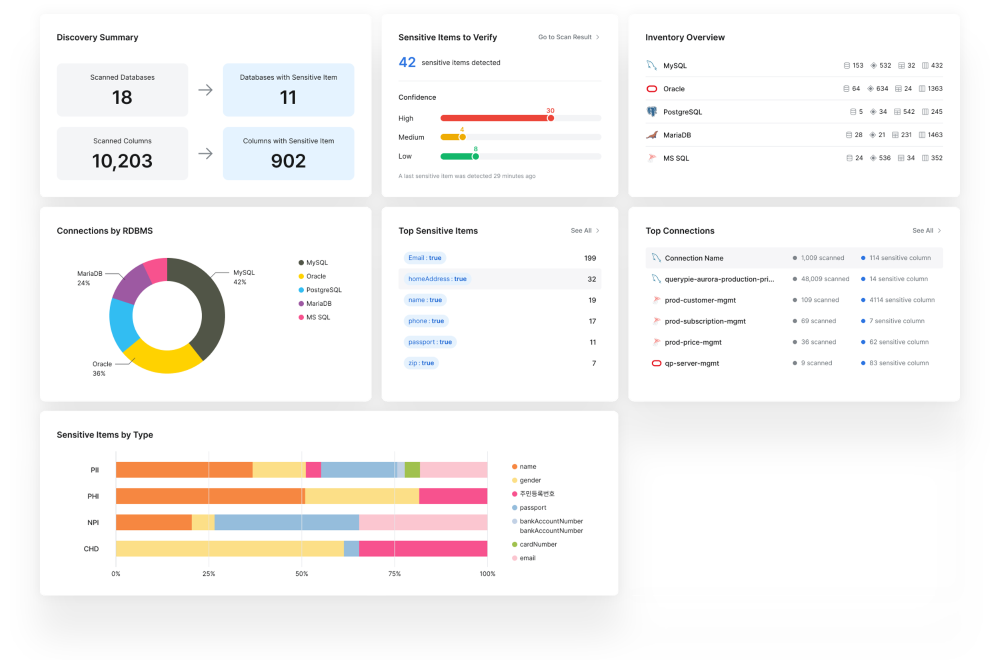
Take control by automatically detecting sensitive information in your data sources on a regular schedule or whenever necessary.
Streamline your compliance efforts by automatically classifying and mapping sensitive information by type, making it easier to address security requirements.
Enhance your security measures through automatic tagging of detected sensitive information, laying the groundwork for effective policy-based access control.
Improve your detection accuracy with identifiers that provide context, helping you uncover targets that traditional methods might miss.
Utilize our dashboard to gain insights into the types and status of detected sensitive information, empowering your data protection strategies.